What is Microsoft Defender for Endpoint?
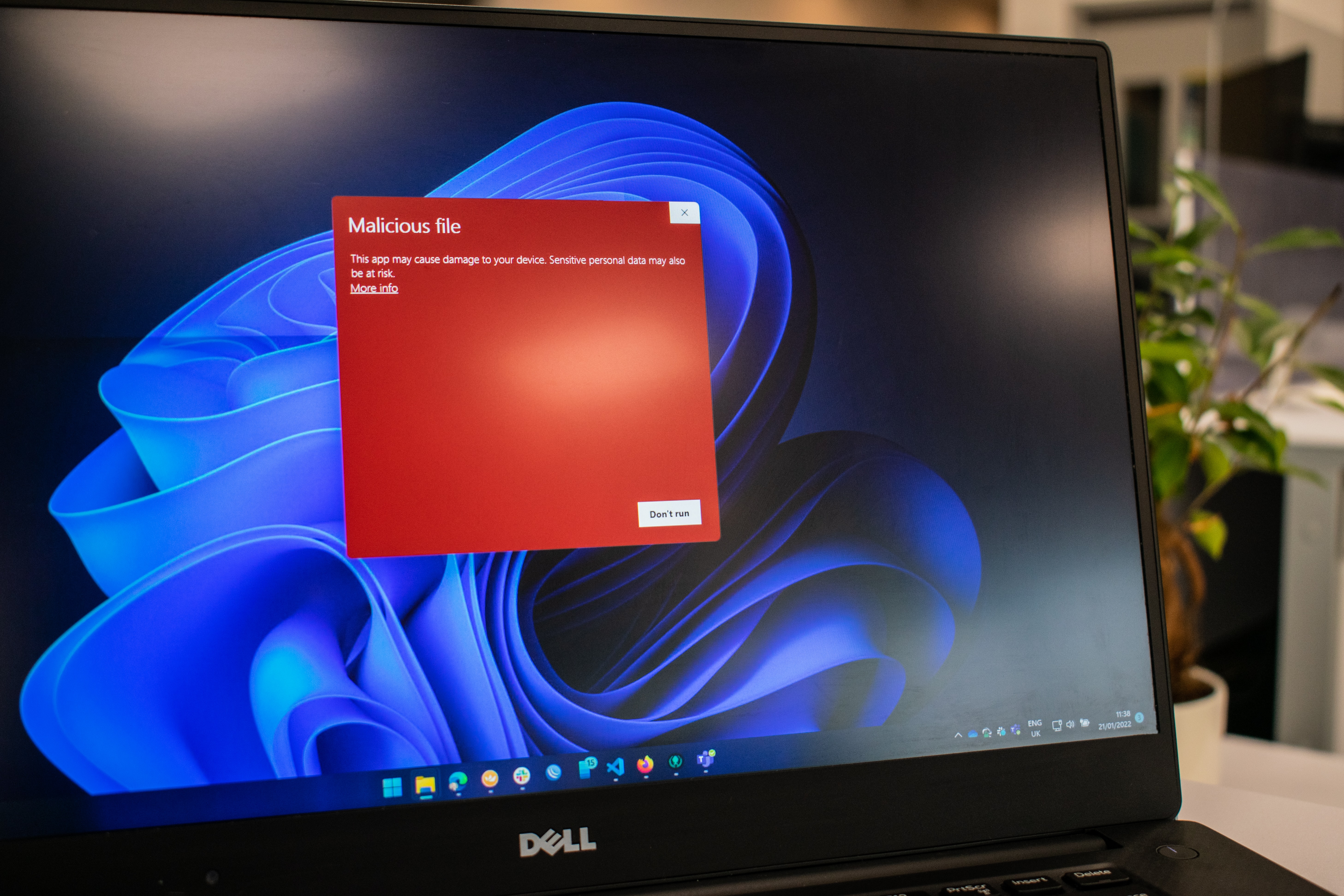
Microsoft Defender provides anti-malware capabilities for Windows systems and should not be confused with Microsoft ATP, which is a solution after hacking , which complements Microsoft Defender AV.
Antivirus software is software that detects, stops and removes various cyber threats such as viruses and Trojans. The simplest form of malware detection is based on signatures. It works by searching for specific known pieces of malware in files. This type of detection can be easily bypassed using techniques called ghostwriting. This is where malware authors add/modify small pieces of code to change the signature of the malware while maintaining all of its functionality. Heuristic-based detection is used to avoid evasion and combat new and unknown malware. Unlike signature-based detection, this type of detection looks for suspicious behavior in software, not just signatures. Microsoft Defender includes both of these detection methods, as well as other features to help identify potential malware.
Key features of Microsoft Defender for endpoint
Real-time protection
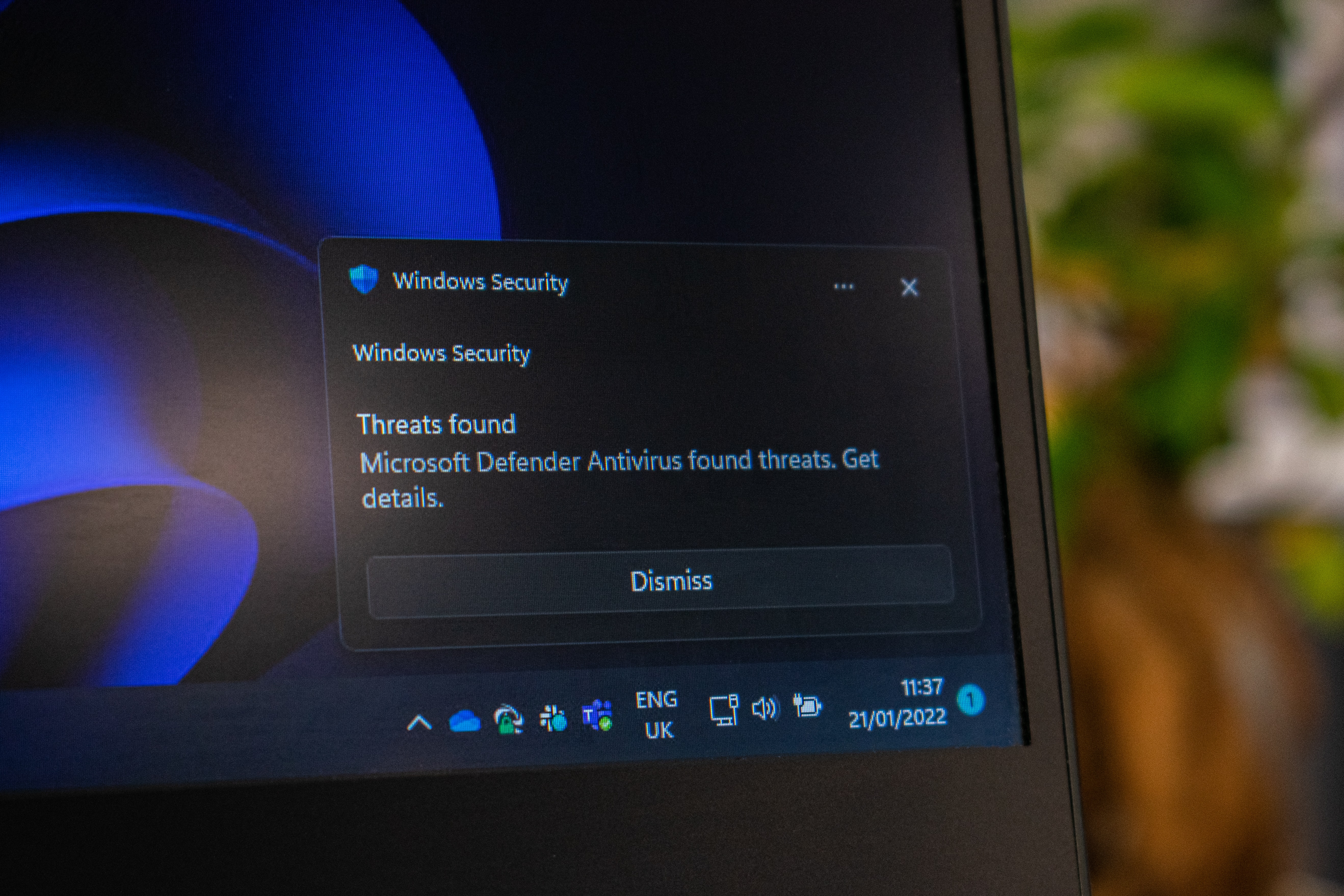
Unlike passive scanning, real-time protection actively searches for malware that is about to be downloaded, copied or executed. Although active, real-time malware scanning requires additional resources, it is invaluable in stopping malware before it can be downloaded or executed.
Cloud protection
It provides additional protection against malware by sending information about suspicious files to Microsoft servers and asking if they are safe to run. When automatic sample submission is enabled, relevant files can be sent to Microsoft, but you can also submit samples manually. This feature will automatically download only executable files. Non-executable files such as documents (even with macros) will not be loaded and parsed. Enabling these features significantly improves the effectiveness of real-time protection. However, even if it doesn't upload personal documents, it could still raise privacy concerns.
Scanning
This is the simplest form of malware protection. Running a Defender scan will passively scan files based on the selected scan type and look for malware. The advantage of scanning is that it usually scans more files than other types of protection. The downside is that it doesn't actively run, meaning it won't stop a virus from being downloaded, for example.
There are different types of scans you can run:
- Quick Scan Looks only at the most common malware locations.
- Full scan scans all the files on your hard drive and usually takes a very long time.
- Selective Scan looks at a location of your choosing, such as a specific file or removable drive.
- Windows Defender Offline Scan , which restarts and scans outside of the normal Windows environment.
Exceptions
Sometimes Defender may remove files that are not themselves malware and that you might want to keep. For example, cryptocurrency mining software and memory editors are regularly detected as malware or potentially unwanted programs. This is for good reason, as these types of software are often used as part of malware. However, there may be legitimate reasons for running this type of software. To resolve this, you can set Windows Defender exclusions for files, folders, file types, and processes that you know are safe.
Exceptions are also sometimes used to prevent real-time resource overload. For example, programmers often exclude their development folders because there is no reason to scan their software every time they test it.
Still have questions?
If you want to set up Microsoft Defender in your organization, just contact us and get advice on issues that interest you.

