Azure Active Directory (Azure AD) is a cloud-based identity and access management service. Azure AD allows your employees to access external resources such as Microsoft 365, the Azure portal, and thousands of other SaaS applications. Azure Active Directory also helps them access internal resources, such as applications on your corporate intranet and any cloud applications developed for your organization.
Azure AD provides different benefits to members of your organization depending on their role:
IT administrators use Azure AD to manage access to applications and application resources according to business requirements. For example, as an IT administrator, you can use Azure AD to require multi-factor authentication when accessing critical organizational resources. You can also use Azure AD to automate user provisioning between your existing Windows Server AD and cloud applications, including Microsoft 365. Finally, Azure AD gives you powerful tools to automatically protect user identities and credentials and meet your access control requirements.
Application Developers can use Azure AD as a standards-based authentication provider that helps them add single sign-on (SSO) to applications that work with existing user credentials. Developers can also use the Azure AD API to create personalized experiences using organizational data.
Microsoft 365, Office 365, Azure or Dynamics CRM Online subscribers are already using Azure AD because every Microsoft 365, Office 365, Azure and Dynamics CRM Online customer automatically becomes an Azure AD tenant. You can start managing access to your integrated cloud applications right away.
What is an Identity Security Assessment?
The Identity Security Score is a percentage that serves as an indicator of how well you meet Microsoft's security best practices. Each action to improve your identity security score is tailored to your specific configuration.
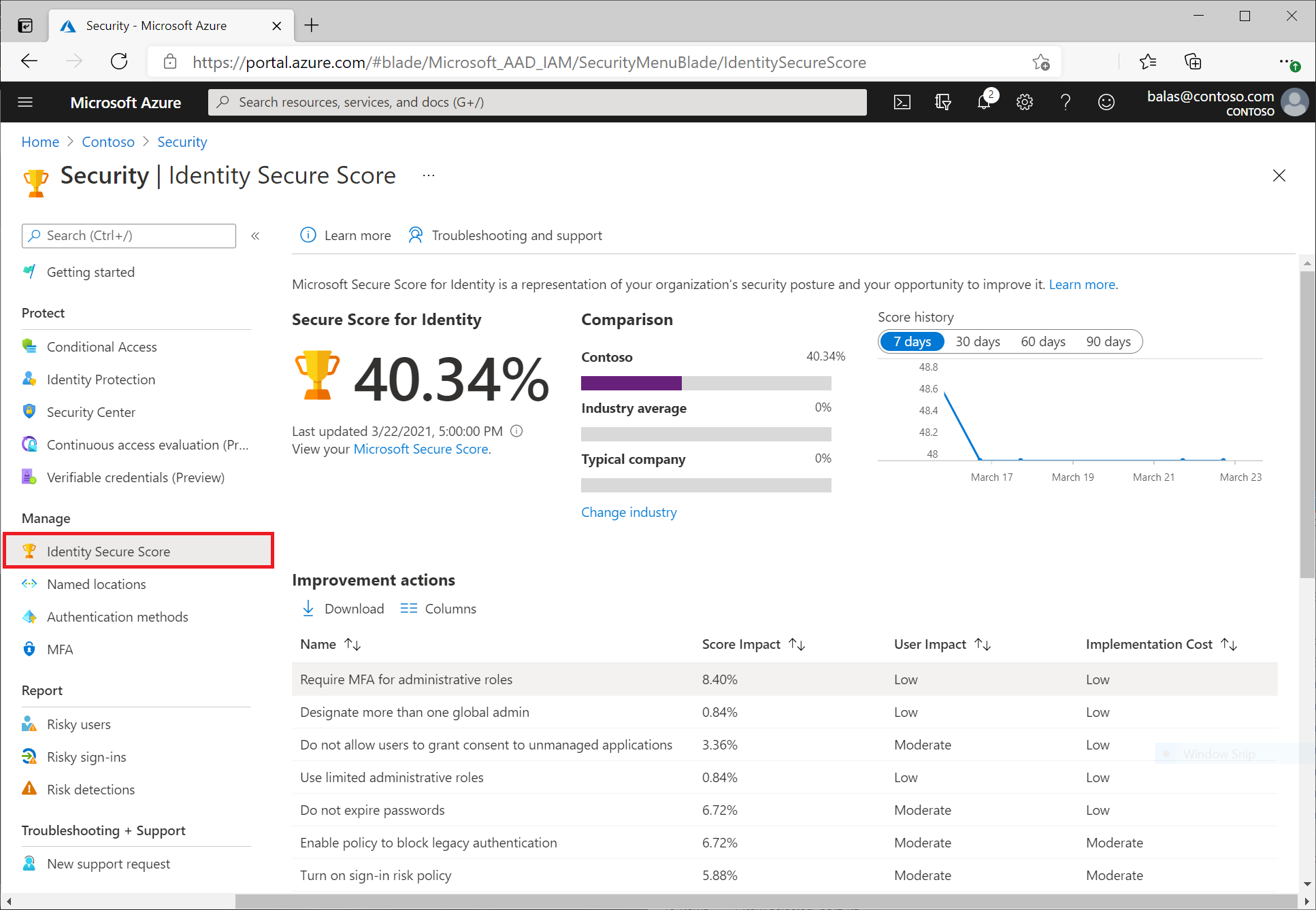
The rating will help you:
- Objectively measure your personal security level
- Plan for identity security improvements
- Measure the success of your improvements
You can access the assessment and related information on the Identity Security Assessment dashboard. On this panel you will find:
- Your assessment of personal security
- A comparison chart showing how your identity security score compares to other tenants in the same industry and similar size.
- A trend graph showing how your assessment of the security of your personal information has changed over time.
- List of possible improvements
By taking improvement actions, you can:
- Improve your security posture and your score
- Take advantage of the features available to your organization as part of your identity investment.
How can you find out your organization's security rating?
Identity security assessment is available in all editions of Azure AD. Organizations can access their identity security score at portal Azure > Azure Active Directory > Safety > Assessing identity security.
How can I improve my Azure AD Identity Security Score?
Here is a list of tips that, if implemented, will significantly improve your organization's security rating.
1. Assign more than one global administrator
Organizations rarely encounter this problem because most have too many global administrator accounts. You should have up to three, and one of them should be an emergency backup account with a 200+ character password and should not be covered by most policies. If you lose access to your account, Microsoft will not be able to return it to you.
2. Use least privileged administrative roles
Here the system simply wants to see that you are using other admin roles besides global admin in some capacity. There are over 50 admin roles to choose from. Give those employees who were previously global administrators only the roles they need.
3. Require multi-factor authentication for administrative roles
To earn the 10 points this item offers, you'll need to create a Conditional Access policy and configure it to require MFA for all admin roles. This is one of the default security policies, so unless you have removed it, it should already be a policy for your tenant.
4. Don't let users consent to untrusted apps
To implement this policy, you must configure an enterprise application policy. If you really want to limit the impact of Shadow IT, include an admin workflow in your policy so that users must seek admin approval to add an application.
5. Change passwords regularly
This may be difficult in some regulated businesses. Many regulatory requirements include mandatory password rotation, but this is no longer best practice as it has been found that users tend to shorten passwords, making them easier to guess.
6. Enable a policy to block legacy authentication
This is another default security setting, so if you haven't removed it, this conditional access policy should already be enabled. If not, consider using the new Conditional Access policy templates. They are really easy to use. You'll find template categories for devices and identities.
7. Protect all users with a sign-in risk policy
It requires your P2 license and will protect your users from suspicious login attempts. This occurs when an unusual event occurs, such as logging in from a different location, using a different device, or connecting to a public Wi-Fi network with a known wrong IP address. Microsoft is keeping the exact logic secret.
8. Protect all users with a risk management policy
This is another case that requires your P2 license, and another case where Microsoft is keeping the exact logic secret. This is where you'll apply a Conditional Access policy, which may block your users from authenticating, or may prompt them for multi-factor authentication a second time when Microsoft detects that the user's behavior is unusual and may not actually be the case.
9. Enable self-service password reset
Microsoft rates this as having a moderate user impact because not only do you, as an administrator, have to configure settings in Azure, but also, if you are using Azure AD Connect To sync your on-premises AD, you also need to enable password writeback. However, once you get past this pain, your users will thank you because they will now have one password for both ads, and with this policy they can reset their own password. However, your help desk will be busy for a while helping people get alternative phone and email addresses registered with MFA.
10. Make sure all users can pass multi-factor authentication
This is the only element listed as having a high impact on the user, but since it is about getting everyone to complete the MFA registration process, it is truly a prerequisite for successful implementation of MFA . Implementing multi-factor authentication eliminates approximately 98 % attacks on user credentials.
Conclusion
Every 48 hours, Azure reviews your security configuration and compares it to recommended best practices. Based on the results of this assessment, a new score is calculated for your catalogue. It may be that your security configuration is not fully compliant with the best practices and the improvement steps are only partially completed. In these scenarios, you will only be awarded a portion of the maximum score available for the control.
But by implementing all the tips above, you will achieve the highest possible Azure Active Directory authentication security score.
Still have questions? Just contact us. Fanetech is a supplier of Microsoft licenses and cloud solutions in Kazakhstan.

