Microsoft Defender for Office 365 includes powerful automated investigation and response (AIR) capabilities that can save your security team time and effort. As alerts are triggered, your security team must review, prioritize, and respond to those alerts. Keeping up with the volume of incoming alerts can be overwhelming. Automating some of these tasks can help.
AIR enables your security team to work more efficiently and effectively. AIR's capabilities include automated investigation processes in response to threats known today. Appropriate remediation actions are pending approval, allowing your security team to effectively respond to detected threats. With AIR, your security team can focus on higher priority tasks without losing sight of important alerts that are triggered.

AIR flow
The trigger is triggered and the security software launches an automated investigation that identifies findings and recommends action. Here is flow AIR, step by step:
- An automatic investigation is initiated in one of the following ways:
- Or the alert is triggered by something suspicious in the email (such as a message, attachment, URL, or a compromised user account). An incident is created and an automatic investigation begins; or
- A security analyst runs an automated investigation when you use Explorer.
- During an automated investigation, the system collects data about the email in question and the objects associated with the email. Such objects may include files, URLs, and recipients. The scope of the investigation may increase as new and related alerts become available.
- During and after an automated investigation, details and results are available for viewing. The results may include recommended actions that can be taken to respond to and resolve any existing threats identified.
- Your security team reviews investigation findings and recommendations, and approves or rejects remediation actions.
- As remediation actions are approved (or rejected), the automatic investigation ends.
In Microsoft Defender for Office 365, no remediation steps are performed automatically. Remediation actions are taken only after approval by your organization's security team. AIR's capabilities save security teams time by identifying remediation actions and providing the information they need to make an informed decision.
During and after each automated investigation, your security team can:
- View investigation alert details
- View investigation details
- Review and approve actions based on the results of the investigation
What triggers trigger automated investigations?
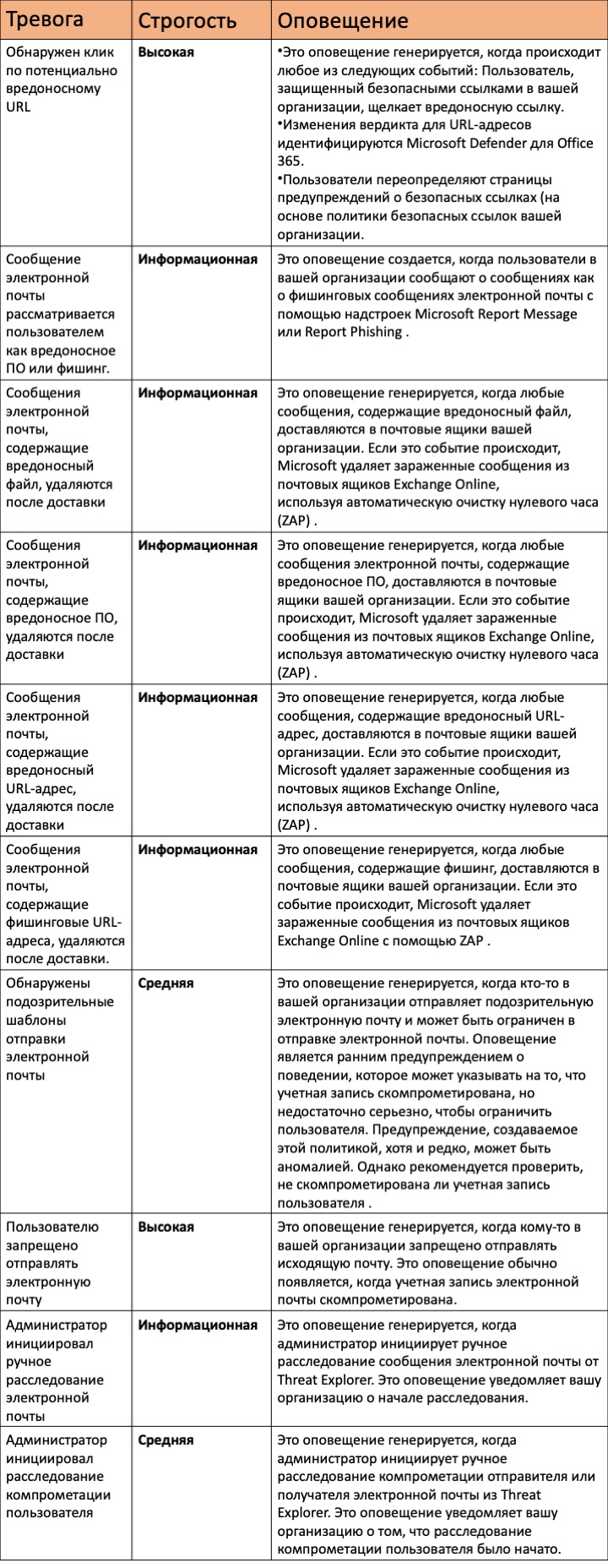
Microsoft 365 provides many built-in alert policies that help identify abuse of Exchange administrator privileges, malware activity, potential external and internal threats, and information governance risks. Some default alert policies may trigger automatic investigations. The following table describes the alerts that trigger automated investigations, their severity in the Microsoft 365 Defender portal, and how to create them.
Required licenses
In Microsoft Defender for Office 365 Plan 2 should be assigned:
- Security administrators (including global administrators)
- Your organization's security team
- End users
Still have questions?
We at Fanetech are engaged in the integration of Microsoft solutions into the IT infrastructure of any business. Just contact us for advice.

